Executive Summary
What was found
- Majority of the users are on the legacy product.
- The legacy product is an on-premise product.
- Customers aren't necessarily the most tech savvy.
- Legacy products have a handy component that could make it forward compatible with the new product.
What it meant
- To retain the customers, we have to bring them to the new cloud based product which is currently being developed and supported.
- Customers's authentication data needs to be ported to the new product for a seamless transition experience.
What's next?
- To build the proof of concept to show that this transition can be done.
- Successfully built the proof of concept involving multiple moving parts, and came up with 3 ways customers could port their data.
The Story...
Background

- RSA Security was the security division of Dell EMC. I worked on their SecurID authentication product.
- RSA had many customers in their legacy product called AxM (Access Manager).
- Their new product was SecurID Access, which was a cloud based authentication product.
- The objective was to see how we could help the legacy customers port their authentication data to SecurID seamlessly.
- Such an offering would enable more flexibility to the customers as they could authenticate their users globally.
The Innovation

- AxM used Apache to get input from the user and authenticate through the servers installed on the system.
- The key was to realise that we don't need an entirely new server side code to use SecurID's services.
- We modified AxM's code such that it forwarded requests to SecurID, instead of the servers on premise.
- The result was a simplified software code that had 33% less moving parts than the proposed design.
- This simplification meant fewer lines of code, hence fewer breaks and failures. This also meant low development cost.
Initial Design
- This was the search phase, where we were looking for ways to efficiently build the robust product.
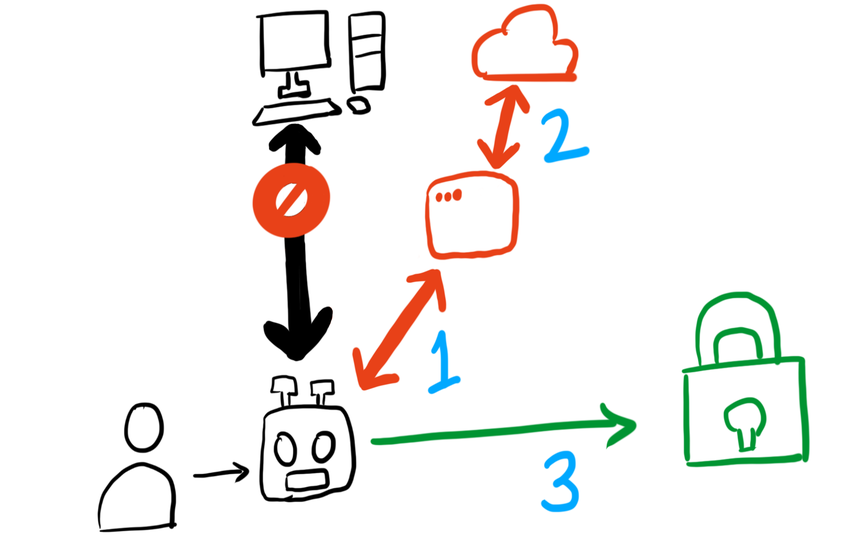
- Human = User
- Robot = AxM (The Old Product)
- Black Computer = On prem authentication servers that AxM talks to, to authenticate, which was not to be used anymore.
- Red Square = Web Browser Component proposed to connect SecurID
- Red Cloud = SecurID Access Cloud (The New Product)
- Green Lock = Protected resource the User is trying to access
- This architecture used 3 steps to accomplish the task.
- Step 1 Make the old product talk to a web server component.
- Step 2 build the web server component to talk to the new product.
- Step 3 based on the result, authenticate the User to the protected resource.
- Protocols and Tools
- 1 used C C++ HTTP UNIX
- 2 used C# .NET cURL JSON
- 3 used Javascript HTML
Design After Innovation
- This was the implementation phase, where we implemented the efficient way to build the robust product.
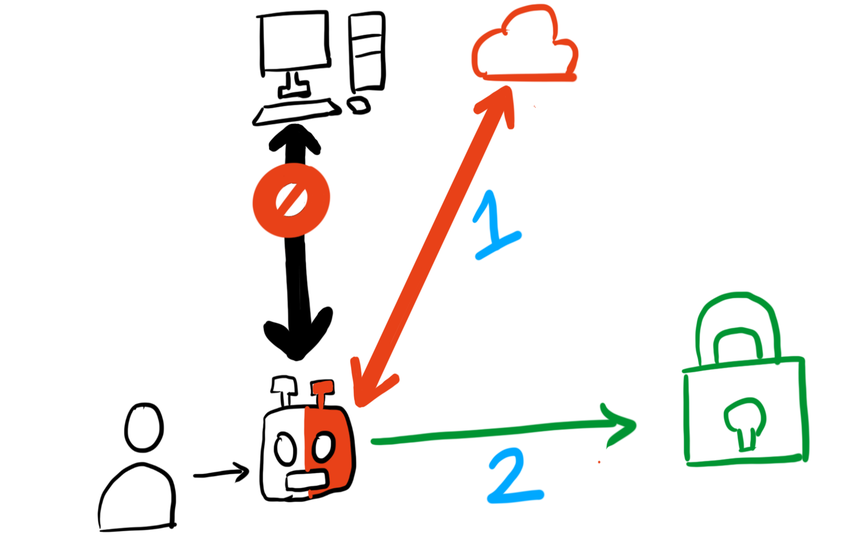
- Human = User
- Half Red Robot = AxM (The Old Product) modified to directly talk to SecurID
- Black Computer = On prem authentication servers that AxM talks to, to authenticate, which was not to be used anymore.
- Red Cloud = SecurID Access Cloud (The New Product)
- This was the architecture we built, it excluded an entire component, making the design more simple as it involved less moving parts.
- Developed architecture was a working AxM talking to SecurID -> Access to resource.
- This architecture used 2 steps to accomplish the task.
- Step 1 The old product talks directly to a new product, eliminating the need for a web server component.
- Step 2 based on the result, authenticate the User to the protected resource.
- Protocols and Tools
- 1 used C C++ HTTP UNIX C# .NET cURL JSON XACML
- 2 used Javascript HTML
Tools Used
- C
- C++
- UNIX Shell Scripting
- Javascript
- JSON
- XACML
- C#
- cURL
- .NET
- HTML





